Blog Posts
- Home /
- Blog Posts
GDPR and DORA Compliance for IAM Systems: A Technical Guide
Identity and Access Management (IAM) systems sit at the intersection of data protection and operational resilience, making them critical components for compliance with both the General Data Protection Regulation (GDPR) and the Digital Operational Resilience Act (DORA). This technical guide explores how to architect and configure IAM systems to meet these regulatory requirements while maintaining security and usability.
Read More
Keycloak vs. Auth0: Enterprise IAM Platform Comparison
Selecting the right Identity and Access Management (IAM) platform is a critical decision for enterprises. Two popular options, Keycloak and Auth0, offer robust capabilities but with different approaches, strengths, and trade-offs. This comprehensive comparison will help enterprise architects and technology leaders make an informed decision based on their specific requirements.
Read More
OAuth 2.0 vs OAuth 2.1: What Enterprise Architects Need to Know
OAuth 2.0 has been the industry standard for authorization since 2012, but the emerging OAuth 2.1 specification aims to address several security vulnerabilities and implementation challenges. For enterprise architects and IAM specialists, understanding these differences is crucial for making informed decisions about authentication infrastructure.
Read More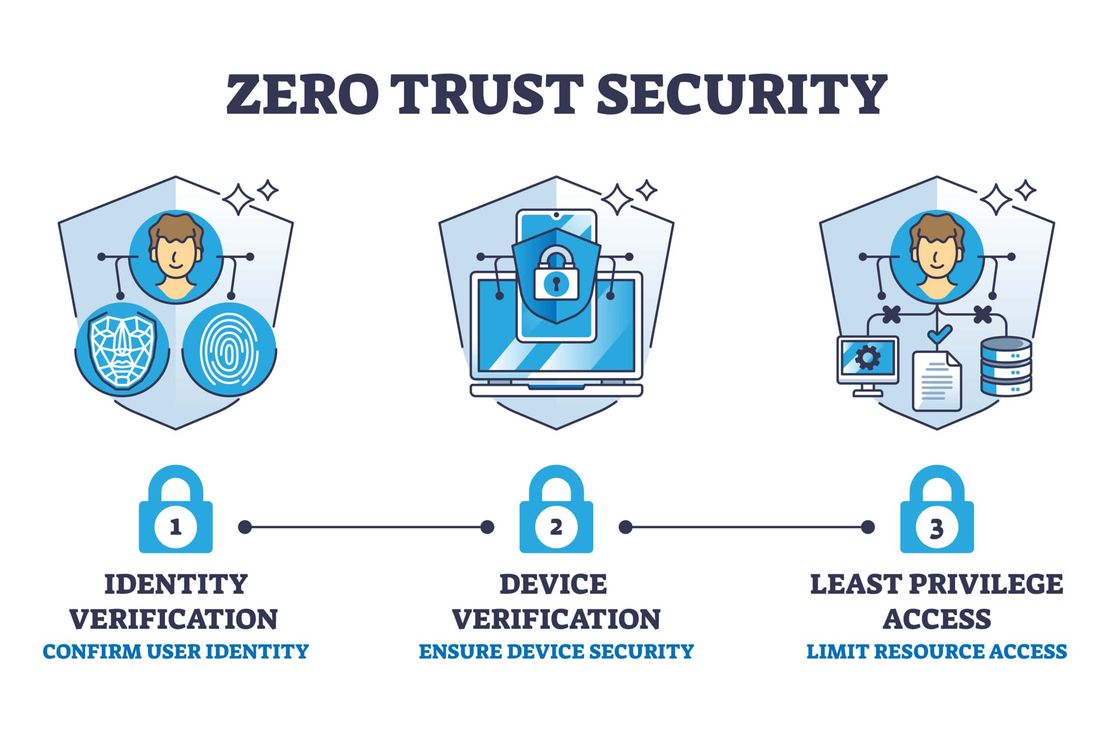
Implementing Zero Trust Architecture with Modern IAM Solutions
In today’s rapidly evolving threat landscape, traditional perimeter-based security models are no longer sufficient. The Zero Trust security model, based on the principle of “never trust, always verify,” has emerged as the gold standard for enterprise security architecture. At the core of any successful Zero Trust implementation is a robust Identity and Access Management (IAM) solution.
Read More