Implementing Zero Trust Architecture with Modern IAM Solutions
- Gustavo Rodríguez
- Security architecture , Zero trust
- September 15, 2023
Table of Contents
In today’s rapidly evolving threat landscape, traditional perimeter-based security models are no longer sufficient. The Zero Trust security model, based on the principle of “never trust, always verify,” has emerged as the gold standard for enterprise security architecture. At the core of any successful Zero Trust implementation is a robust Identity and Access Management (IAM) solution.
Understanding Zero Trust Architecture
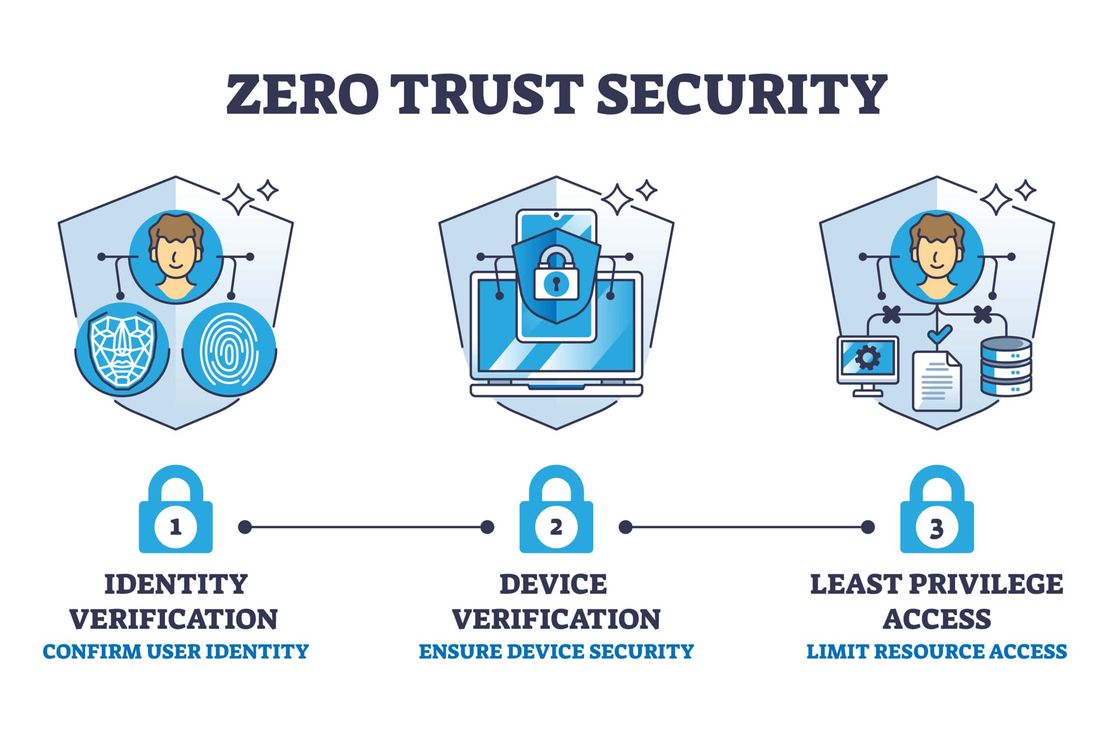
Zero Trust Architecture (ZTA) is a security concept centered on the belief that organizations should not automatically trust anything inside or outside their perimeters. Instead, they must verify anything and everything trying to connect to their systems before granting access.
Key principles of Zero Trust include:
- Verify explicitly: Always authenticate and authorize based on all available data points
- Use least privilege access: Limit user access with Just-In-Time and Just-Enough-Access
- Assume breach: Minimize blast radius and segment access, verify end-to-end encryption, and use analytics to improve security posture
“Zero Trust is not a product or a specific technology; it’s a strategic approach to security that eliminates implicit trust and continuously validates every stage of digital interaction.” - National Institute of Standards and Technology (NIST)
IAM as the Foundation of Zero Trust
A modern IAM solution serves as the cornerstone of Zero Trust by providing:
1. Strong Authentication
Multi-factor authentication (MFA) is non-negotiable in a Zero Trust model. Modern IAM solutions support various authentication factors:
- Something you know (passwords, PINs)
- Something you have (mobile devices, hardware tokens)
- Something you are (biometrics)
- Contextual factors (location, device health, behavior patterns)
2. Continuous Authorization
Zero Trust requires continuous verification rather than one-time authentication. This means:
- Continuous session validation
- Risk-based authentication that adapts to changing contexts
- Real-time policy enforcement
3. Fine-Grained Access Control
Implementing the principle of least privilege through:
- Attribute-Based Access Control (ABAC)
- Role-Based Access Control (RBAC)
- Just-In-Time access provisioning
- Micro-segmentation of resources
Implementation Roadmap
Implementing Zero Trust with IAM requires a phased approach:
Assessment Phase
- Identify critical data assets and systems
- Map existing identity infrastructure
- Document current access patterns and policies
Design Phase
- Define Zero Trust policies and controls
- Select appropriate IAM technologies
- Design authentication and authorization workflows
Implementation Phase
- Deploy modern IAM solutions (Okta, Auth0, Azure AD, etc.)
- Implement MFA across all access points
- Establish continuous monitoring capabilities
Optimization Phase
- Refine policies based on user behavior analytics
- Implement automated response to suspicious activities
- Continuously test and validate security controls
At AuthMasters, we specialize in guiding enterprises through this transformation journey, ensuring your Zero Trust implementation is both robust and user-friendly.