
OAuth 2.0 vs OAuth 2.1: What Enterprise Architects Need to Know
OAuth 2.0 has been the industry standard for authorization since 2012, but the emerging OAuth 2.1 specification aims to address several security vulnerabilities and implementation challenges. For enterprise architects and IAM specialists, understanding these differences is crucial for making informed decisions about authentication infrastructure.
Read More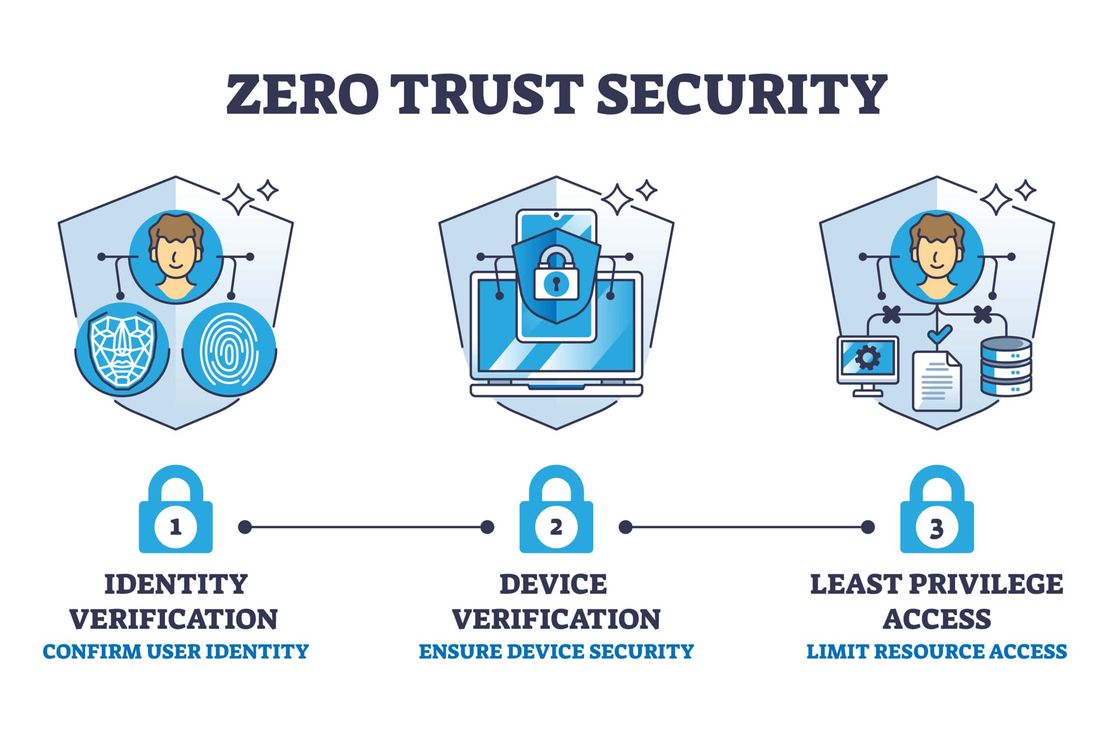
Implementing Zero Trust Architecture with Modern IAM Solutions
In today’s rapidly evolving threat landscape, traditional perimeter-based security models are no longer sufficient. The Zero Trust security model, based on the principle of “never trust, always verify,” has emerged as the gold standard for enterprise security architecture. At the core of any successful Zero Trust implementation is a robust Identity and Access Management (IAM) solution.
Read More